Transparent Proxies
In today’s digital world, managing network traffic efficiently while ensuring security is a top priority. Transparent proxies are a key solution, acting as invisible intermediaries that handle web requests without requiring user configuration. This guide explores what transparent proxies are, how they function, and why they’re valuable for modern networks.

How Transparent Proxies Work
A transparent proxy intercepts web traffic at the network level—typically via a gateway or firewall—without altering the request or response. Users connect to the internet as usual, unaware of the proxy’s presence. The proxy then forwards requests to the destination server and returns the responses, often performing tasks like filtering or caching in the background.
Use Cases for Transparent Proxies
Transparent proxies are versatile tools with applications across various settings:
Web Filtering: Block access to unwanted or unsafe websites, such as in schools or workplaces.
Content Caching: Store popular web content locally to speed up access and save bandwidth.
Network Security: Scan traffic for threats, block malicious sites, or enforce access policies.
Traffic Monitoring: Log user activity for compliance or troubleshooting purposes.
For example, a business might use a transparent proxy to prevent data leaks, while an ISP could optimize performance with caching.
Benefits and Limitations
Transparent proxies offer distinct advantages but also have drawbacks:
Benefits:
No Configuration Needed: Works seamlessly without user setup.
Centralized Management: Simplifies network-wide policy enforcement.
Performance Boost: Reduces load times via caching.
Limitations:
Privacy Issues: Users may not know their traffic is monitored.
Potential Latency: Improper setup can slow down connections.
Compatibility: Some protocols or apps may not work smoothly.
Organizations must balance these factors based on their needs.
Transparent Proxies vs. Other Proxy Types
Here’s how transparent proxies compare:
Explicit Proxies: Require manual setup and are visible to users.
Reverse Proxies: Protect servers by managing incoming traffic.
Anonymous Proxies: Mask user identity from websites.
Transparent proxies stand out for their invisibility and ease of use in controlled environments.
Implementing Transparent Proxies with IPFLY
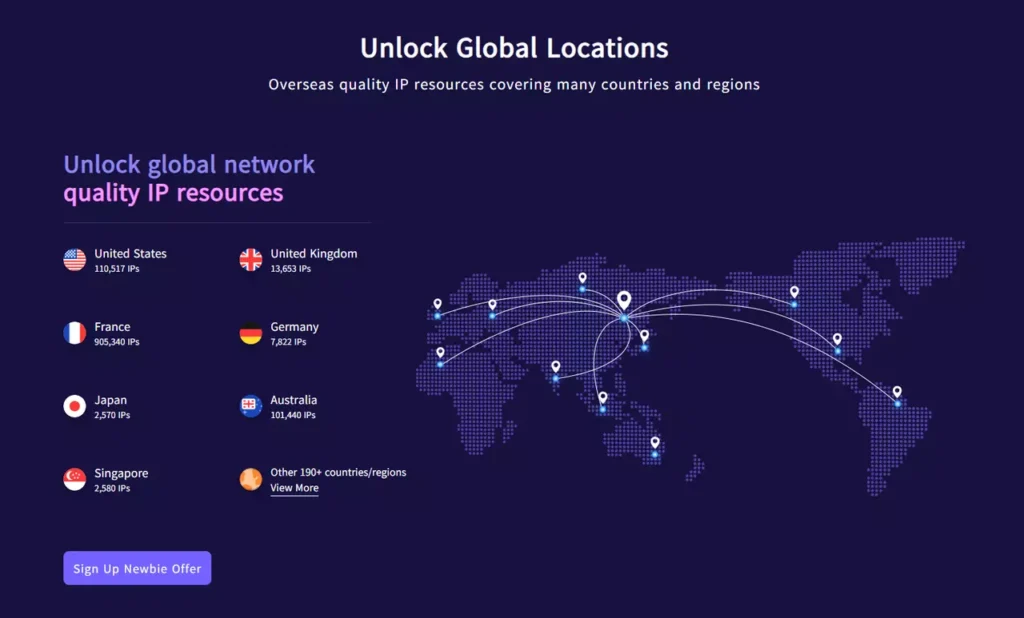
For top-tier transparent proxy solutions, IPFLY delivers. IPFLY’s services integrate effortlessly into your network, offering advanced web filtering, fast caching, and robust security features. With a global proxy network, IPFLY ensures minimal latency and maximum reliability—perfect for businesses scaling their operations.

Transparent proxies are essential for balancing security, performance, and control in network management. By leveraging solutions like those from IPFLY, organizations can optimize their networks while keeping users safe and productive. Understanding their strengths and limitations helps you deploy them effectively.


